ADFS provides Single Sign On for multiple Web Applications by using Active Directory account. ADFS sends a claim to a web application in behalf of Active Directory.
How it works:
User tries to log on to a web application
Web Application Server redirect that request to ADFS
ADFS checks with Active Directory and AD authenticates the user
ADFS issues the claim
Web Application accepts the claim
User has access to the system
Note:During this process, no username or password is passed among the servers. The claim has Active Directory attribute/s. That attribute can be first name, last name or a custom attribute.
Creating ADFS Certificate:
For production AD FS farms a publicly trusted SSL certificate is recommended. This is usually obtained by submitting a certificate signing request (CSR) to a third party, public certificate provider.
My ADFS farm will be working on the local network, so I will create my own certificate from my own CA. If you don't have a Certification Authority in your domain you can follow my post: Setting Up Microsoft Active Directory Certificate Services
I will have 2 ADFS servers, 2 Web Proxies and 1 separate SQL Server in this lab.
Let’s start.
First I need to create a certificate template for ADFS on the CA Server.
Click on Certificate Templates. Here we see the enabled certificate templates currently. We need to create and enable a new template for ADFS.
Right click Certificate Templates > Click Manage

Right click Web Server certificate and Duplicate it.

Select General and change the name of the certificate as you wish
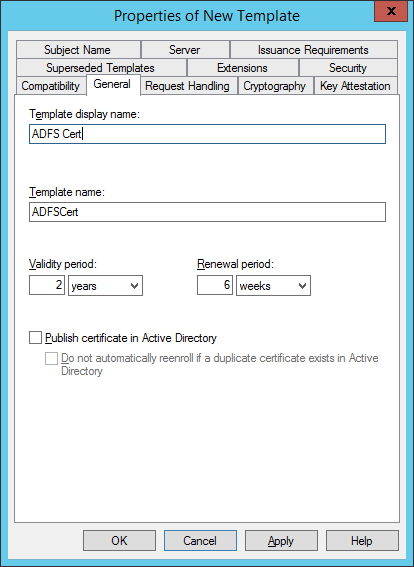
Select Subject Name Tab and choose Supply in the request

Select Request Handling Tab and put a tick “Allow private key to be exported”. This is important because we will export this certificate from first ADFS server and import to the other additional ADFS servers.

We need to give the server permission to enroll for the certificate. Select Security Tab> Add > click Object Types and tick Computers.
I add all my ADFS servers.

Make sure you select Enroll for all your adfs servers that will use ADFS certificate.

Now go back to the main window of Certificate Services. Choose Certificate template to Issue.
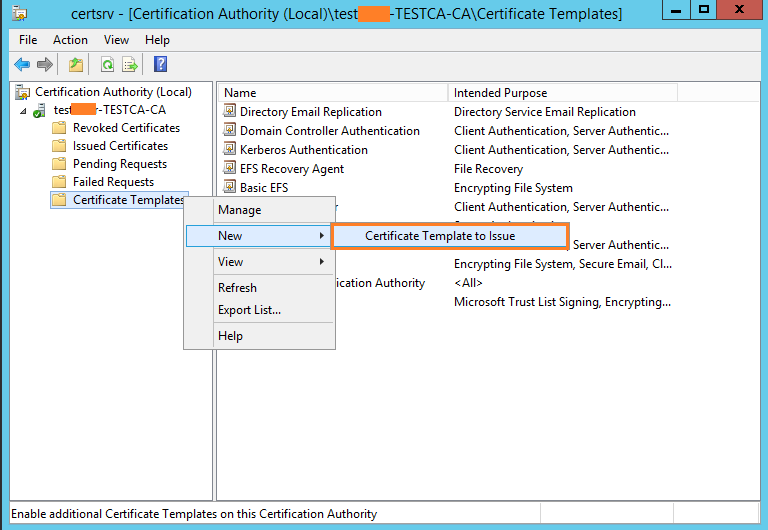
Select the template we just created and hit OK. This will enable this certificate template on this Certification Authority.

If you notice our new certificate is listed under the Certificate Templates.

Certificate Enrollment:
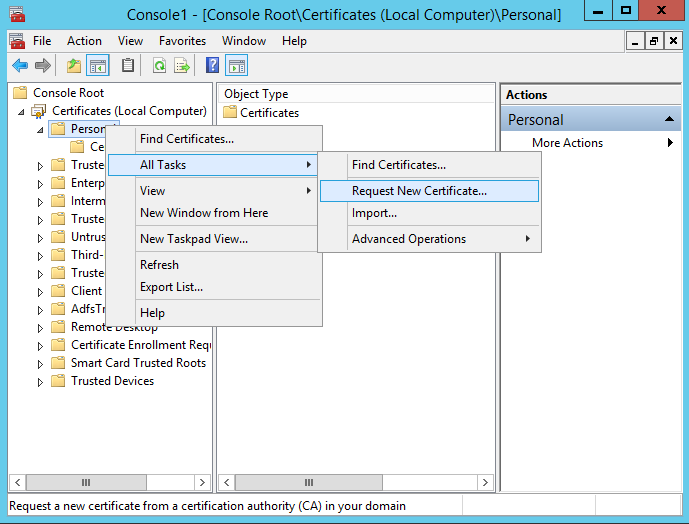
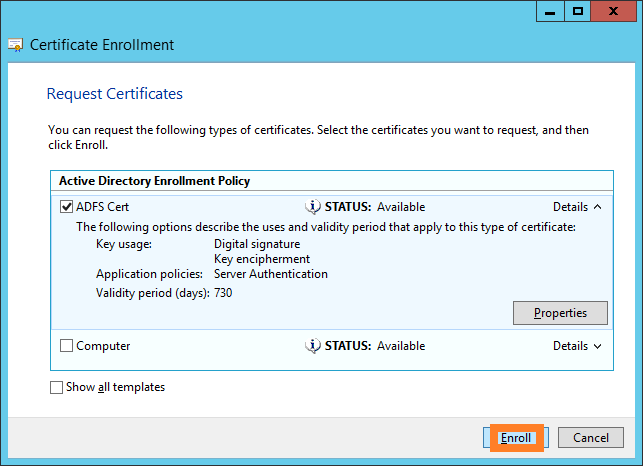
Log on to your first ADFS server and open up mmc and request a certificate from CA.
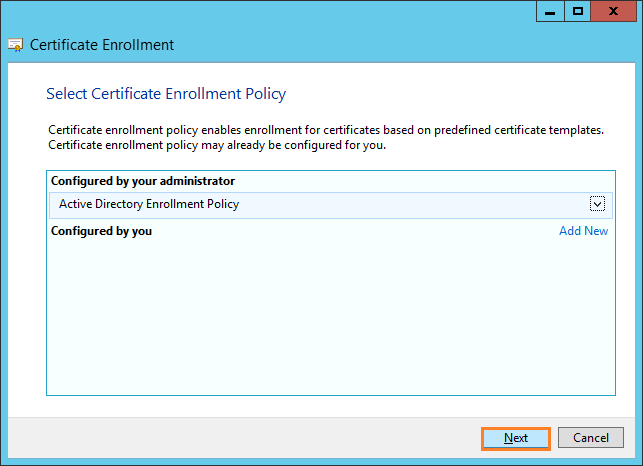
Just click Next
Click More Information link to configure certificate settings

Subject Name> Type should be chosen as Common name.
Enter your desired ADFS Service Name into the Value field and click Add. (I entered testadfs.mydomain.local)
Click OK

and Enroll.
Exporting The Certificate:
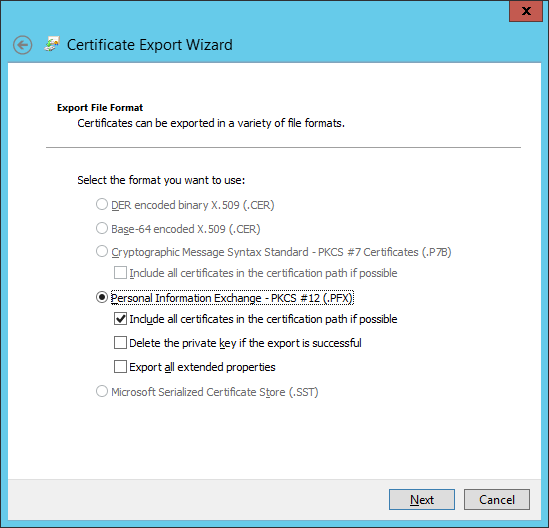
We will import and use this certificate on all our ADFS servers. Therefore we need to export it from the first ADFS server.

Choose "Yes, export the private key"

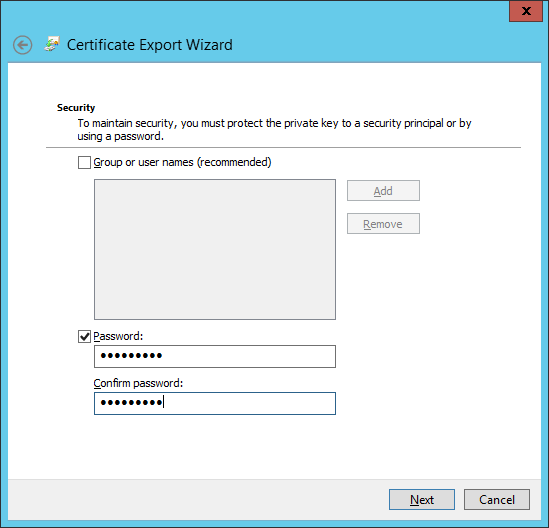
Type a password for the private key
We can import the exported certificate onto second ADFS Server and web Proxy Servers, now.
